Today, the DST Root CA X3 certificate expired, leaving many devices on the internet having issues connecting to services and certificates that use this Root CA, including those using Let’s Encrypt certificates.
Some of these problematic devices include Samsung Galaxy phones, iPhones, VDI zero and thin clients, and even Sophos UTM firewalls.
In my environment, I noticed a number of issues when browsing to websites that use the free Let’s Encrypt certificates, as the Web Protection Web Filtering service on my Sophos UTM firewall would report the certificate has expired and not allow me access to the websites using it.
The Problem
Let’s Encrypt originally used the “DST Root CA X3” certificate to issue Let’s Encrypt certificates. However, as time has passed and the service has been used more, they now use “ISRG Root X1” and “ISRG Root X2” as Root CA’s and “Let’s Encrypt R3” as an intermediate certificate.
Older devices may be using the older Root CA which expired today (September 30th, 2021). Please see https://letsencrypt.org/docs/dst-root-ca-x3-expiration-september-2021/ for more information.
The Fix
To fix this issue, you need to add the 2 new Root CAs to your computer or device.
Root CA Certificates (PEM format):
Intermediate Certificate (PEM format):
You can download them by clicking the links above or go to https://letsencrypt.org/certificates/ for more information and to download if you don’t trust the above links.
After downloading and adding these Root CAs and the Intermediate CA to your computer or device, you should have the full certificate chain to validate the Let’s Encrypt certificates. The Let’s Encrypt certificates that are used on websites that you visit and that you might have deployed on your servers should now work without any issues.
If you’re still having issues, you can try deleting the “DST Root CA X3” certificate from your existing Root CAs. Also, you may need to close and reopen any software and/or browsers for it to work with the new certificate.
HTTPS Scanning/Filtering Firewall Fix (Sophos UTM as example)
If you have a firewall that scans HTTPs traffic, you’ll need to add the above certificates to the HTTPS Certification authority list.
As an example, to fix this on the Sophos UTM firewall, follow the instructions below:
- Download the 3 certificates above.
- Log on to your Sophos UTM
- Navigate to “Web Protection”, “Filtering Options”, and “HTTPS CAs” tab.
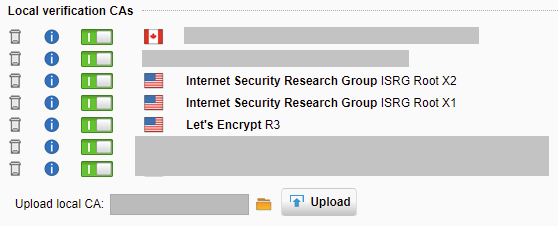
- Disable the old “Digital Signature Trust Co. DST Root CA X3” Certificate in the list.

- Using the “Upload local CA”, browse to and select 1 of the 3 certificates, then click upload.
- Repeat step 5 for each of the 3 certificates listed above.
- The issue has been fixed! You should now see all 3 certificates in the “Local verification CAs” list.
The steps should be similar for other firewalls that provide HTTPS Scanning and Filtering.