Hoje, o certificado DST Root CA X3 expirou, deixando muitos dispositivos na Internet com problemas para se conectar a serviços e certificados que usam essa CA raiz, incluindo aqueles que usam certificados Let’s Encrypt.
Alguns desses dispositivos problemáticos incluem telefones Samsung Galaxy, iPhones, VDI zero e thin clients e até mesmo firewalls Sophos UTM.
No meu ambiente, notei uma série de problemas ao navegar em sites que usam os certificados gratuitos Let’s Encrypt, incluindo e-Social e alguns serviços do governo, pois o serviço Web Protection Web Filtering em meu firewall Sophos UTM relataria que o certificado expirou e não me permite acesso aos sites que o usam .
O PROBLEMA
Let’s Encrypt originalmente usou o certificado “DST Root CA X3” para emitir certificados Let’s Encrypt. No entanto, à medida que o tempo passou e o serviço não foi mais usado, eles agora usam “ISRG Root X1” e “ISRG Root X2” como CA de raiz e “Let’s Encrypt R3” como um certificado intermediário.
Dispositivos mais antigos podem estar usando a CA Root mais antiga, que expirou hoje (30 de setembro de 2021). Consulte https://letsencrypt.org/docs/dst-root-ca-x3-expiration-september-2021/ para obter mais informações.
SOLUÇÃO
Para corrigir esse problema, você precisa adicionar as 2 novas CAs raiz ao seu computador ou dispositivo.
Certificados de CA raiz (formato PEM):
ISRG Root X1 (ou ISRG Root X1 DER Format)
ISRG Root X2 (ou ISRG Root X2 DER Format)
Certificado Intermediário (PEM format):
Let’s Encrypt R3 (Or Let’s Encrypt R3 DER Format)
Você pode baixá-los clicando nos links acima ou ir para https://letsencrypt.org/certificates/ para mais informações e fazer o download, se você não confiar nos links acima.
Depois de baixar e adicionar essas CAs raiz e a CA intermediária ao seu computador ou dispositivo, você deve ter toda a cadeia de certificados para validar os certificados do Let’s Encrypt. Os certificados Let’s Encrypt que são usados em sites que você visita e que você pode ter implantado em seus servidores agora devem funcionar sem problemas.
Se ainda estiver tendo problemas, você pode tentar excluir o certificado “DST Root CA X3” de suas CAs raiz existentes. Além disso, pode ser necessário fechar e reabrir qualquer software e / ou navegador para que funcione com o novo certificado.
Correção do firewall para verificação / filtragem de HTTPS (Sophos UTM como exemplo)
Se você tiver um firewall que verifica o tráfego HTTPs, precisará adicionar os certificados acima à lista de autoridade de certificação HTTPS.
Por exemplo, para corrigir isso no firewall Sophos UTM, siga as instruções abaixo:
Baixe os 3 certificados acima.
Faça logon no seu Sophos UTM
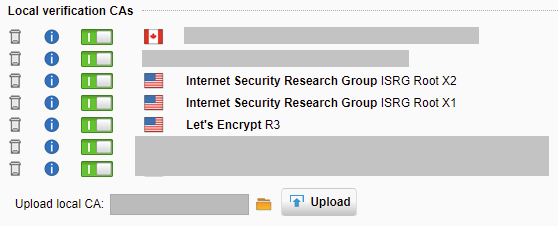
Navegue até a guia “Web Protection”, “Filtering Options” e “HTTPS CAs”.
Desative o antigo certificado “Digital Signature Trust Co. DST Root CA X3” na lista.
Usando “Carregar CA local”, navegue até e selecione 1 dos 3 certificados e clique em carregar.
Repita a etapa 5 para cada um dos 3 certificados listados acima.
O problema foi corrigido! Agora você deve ver todos os 3 certificados na lista “CAs de verificação local”.
As etapas devem ser semelhantes para outros firewalls que fornecem varredura e filtragem HTTPS.